THREAT MODELING METHODOLOGIES
ThreatModeler is the leading automated threat modeling solution that protects an enterprise’s SDLC by identifying and predicting threats, and defining security controls for mitigation. Security and DevOps teams are empowered to make proactive decisions and minimize overall risk by leveraging holistic views of the attack surface.
Redefine your idea of enterprise security and experience the power of automated threat modeling. Complete the form to sign up for a live demo with a threat modeling expert.
When selecting a threat modeling approach, it is critical for businesses to understand that not all solutions are the same. There are various threat modeling methodologies used for enhancing cybersecurity practices, each with various outputs. CISOs and other security subject matter experts should comprehend which method aligns with their specific business goals and objectives to maximize its effectiveness.
OUR METHODOLOGIES
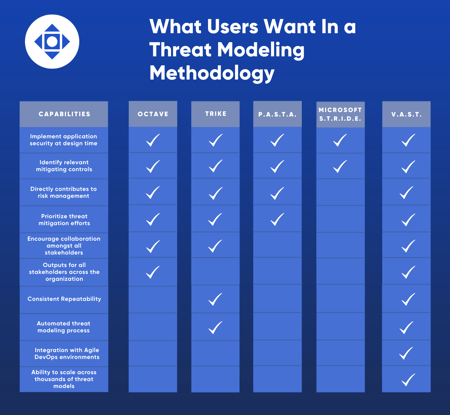
Here are five commonly used threat modeling methodologies to educate decision makers on what's available
One of the first threat modeling methodologies created, Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) focuses on assessing operational risk and security practices rather than technology. This methodology uses a self-directed approach, which means creating and implementing security strategies falls directly on internal IT teams.
This highly customizable approach allows organizations to direct, prioritize, and manage security practices for themselves, making OCTAVE threat modeling useful for creating risk-aware corporate cultures. However, this asset-centric approach to threat modeling focuses on business risk and does not scale well for large organizations.
In 1999, Microsoft introduced the STRIDE threat modeling methodology for Windows software developers to identify security threats during the design process of applications. These security threats include Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, and Elevation of privilege. Security teams can use threat models to check applications against the STRIDE threat classification scheme to identify and mitigate security risks.
Microsoft TMT, which is based on the DFD approach, has severe limitations such as needing the manual efforts of security experts to leverage it, lack of interoperability, and the inability to work collaboratively. These limitations mean TMT cannot realistically be scaled or performed at the speed that modern operational environments require.
PASTA threat modeling is a seven-step Process for Attack Simulation and Threat Analysis. This risk-centric methodology aligns business objectives with technical requirements to provide organizations asset-centric mitigation strategy. PASTA allows security experts to understand the attacker perspective on applications and infrastructure better, and then develop threat management, enumeration, and scoring processes.
The risk and business impact analysis aspect of PASTA threat modeling can elevate into a strategic business exercise for key decision makers rather than just a software development practice for IT teams.
The TRIKE threat modeling methodology uses a unique security auditing process from the perspective of risk management. Before security teams create threat models, stakeholders collectively assign accepted levels of risk to each asset class, creating a “requirements model.” After analyzing the requirements model, security experts produce a threat model.
Threats are then enumerated, and appropriate risk values are assigned from which users create attack graphs and controls to address prioritized threats. Finally, a risk model is generated based on asset, roles, actions, and calculated risk exposure. Trike uses DFDs to show how data flows in an information system. Trike does not easily scale with larger information systems.
The VAST methodology is an acronym for Visual, Agile, and Simple Threat modeling. In today’s world, threat modeling methodologies are only viewed as effective if they scale across the infrastructure and entire DevOps portfolio, integrate seamlessly with an Agile environment, and provide actionable outputs for key stakeholders, with or without technical expertise.
Automation, integration, and collaboration are the three pillars of scalable threat modeling that are foundational to the VAST methodology. These processes help establish a sustainable self-service threat modeling practice driven by DevOps teams that scale across thousands of threat models.
To provide actionable outputs for key stakeholders, VAST addresses different layers of security concerns of development and infrastructure teams using two types of threat models. Application threat models help DevOps to address security concerns when designing applications, while operational threat models allow infrastructure teams to visualize and mitigate threats across an organization’s infrastructure. Specific security expertise is not required when creating or using these threat models due to unique application and infrastructure visualization schemes like process flow diagrams.
The VAST methodology is ideal for enterprise businesses seeking actionable threat models that are unique to the needs of various stakeholders. ThreatModeler, the first commercially available automated threat modeling tool, utilizes the VAST methodology to identify threats based on a customizable, comprehensive threat library. The platform is intended to unify DevOps in collaboration across all organizational stakeholders.
